
The more people that join the Kodi third party add-ons chat on social media the more things get blown out of proportion. Member numbers on some of the social media groups are at an all time high which leads to the panic and fear that the days of Kodi and getting all your TV and movies for free is over, but what did you expect from people that have never seen this happen before? For those like myself that have been engaged in the Kodi platform and all that, it can do will know that this is not new territory, that we have been here before and that eventually, the storm passes. There is no need for panic, these things do and will continue to happen just like they have in the past.
What has happened?
Dish TV is attempting to sue TVAddons and Zem TV for using/reproducing their content. The fallout of this lawsuit is that a number of the Kodi Addon creators have hung up their keyboards only this time...they mean it. Or do they? Of course, they don't mean it. These people are normal people and the only thing they have in their lives to make them feel significant or important is add-on development. They aren't walking away from that. What you will find happening is they will take a short break and return under a new identity ready to push out a new product. Even if they don't there are new developers ready to fill the voids. This is the cat and mouse game of piracy that has been running for years. It's like whack a mole, they hit one mole and another one pops up somewhere else.
So here is where we are!

Covenant = Exodus
The Exodus add-on is no longer being maintained by the developers. The developers of Exodus have just released the Covenant add-on. It looks and functions exactly like Exodus.
We highly recommend opening BUILDS AND UPDATES and doing a Fresh Install (Fresh Install will delete all of your favorites, Addons you have added, Real Debrid and BoomBoom TV username and password. This will remove the Exodus add-on and replace it with the Covenant add-on.
You are free to not install this update and to continue to use Exodus. However, over the next few weeks, it will get less and less sources and will eventually die. We highly recommend jumping on board with Covenant instead of sticking to a dying add-on.
IMPORTANT - Covenant was released less than 12 hours ago. It has a minor bug where it will crash Kodi the first time it is searching for sources for links. After this initial crash, it will work perfectly fine. The developers are aware of this and are going to push an update to fix this issue.
You are able to install Real Debrid exactly the same way you did in Exodus.

The end of Kodi the start of KDPlayer v5
While everyone is running around flapping about the end of Kodi we are quietly getting on with Version 5 of our KDPlayer.
This upgrade of our software is the biggest project we will have undertaken to date. The main objective is as always to provide the user with all the streaming content and android goodies all in one easy to navigate place but the backend support system will also be massively improved with added options and features that will allow us to react quicker to changes in the market.
We won't be going in to too much detail in this post about the interface and everything that it can do but what we will be giving away some of the secrets we have been keeping from you.
The end of Kodi
I just want to quickly touch in this subject before we dive in with the KDPlayer v5 news.
This is not the end of Kodi and third party addons. Sure, a few have hung up their developers hats but make no mistake this is not the end. New addons are born, they age and then they disappear. That is the nature of Kodi and third party addons. It happens all the time.
Dish TV network has flexed their muscles and some developers have run for the hills. I promise you this, once the developer gets to hills he will assume a new identity and jump in the first taxi back to where they came from. All this will do is strengthen the Kodi addon developers. They take the lessons and they learn from them. They will come back stronger and better than ever because nothing unites people better than a common enemy. At the moment the end of Kodi is nothing more than click bait to get you to visit some google advert and some poor content.
Just in case there are any uncertain times within the Kodi community in v5 we have removed the need to rely on Kodi for streaming services. There is always more than one way to skin a cat.
What's new in v5 for the users?
Pretty much everything. The user interface, or UI, has been totally re designed and has been ascetically enhanced. We have followed the lead of 2 of the most popular launchers in regards to layout and delivering the content.
The same options will be available, apps, Kodi Builds, gaming, BoomBoom TV but the content will be displayed better and there will be way more of it. The gaming section has been totally redesigned and will be almost complete with thousands of ROM's to load for your favorite consoles from yesteryear.
What's new in v5
This is where the work is really going in to the software. A whole new interface with way more features.
I know what you're thinking, "Something new to have to learn" yes, but it will be worth while.
Push notifications not just to all users but individual devices too. Need to get in touch with us? you can message us directly and we can message you back.
Universal RSS feeds for the builds. We will be able to have custom messages and have it passed in to any build that the user downloads.
Better settings options, rather than just linking to the Android Settings, which universally was very good, we will be linking to sections of the settings in Androids. Direct links to connection settings, display settings, app settings and all the common items that a user would need to access.
That's everything we can tell you so far....
There is so much more we could tell you now but we don't want to let the cat out of the bag just yet. We have always kept the bulk of our work secret up until the time of release. At this stage we are on target for a beta release towards the end of the month, final release early August.
Thanks for reading, next time we post we will be including some screen shots for you to consume.
PS - it's not the end of Kodi 🙂
Stay Calm and Stream On!
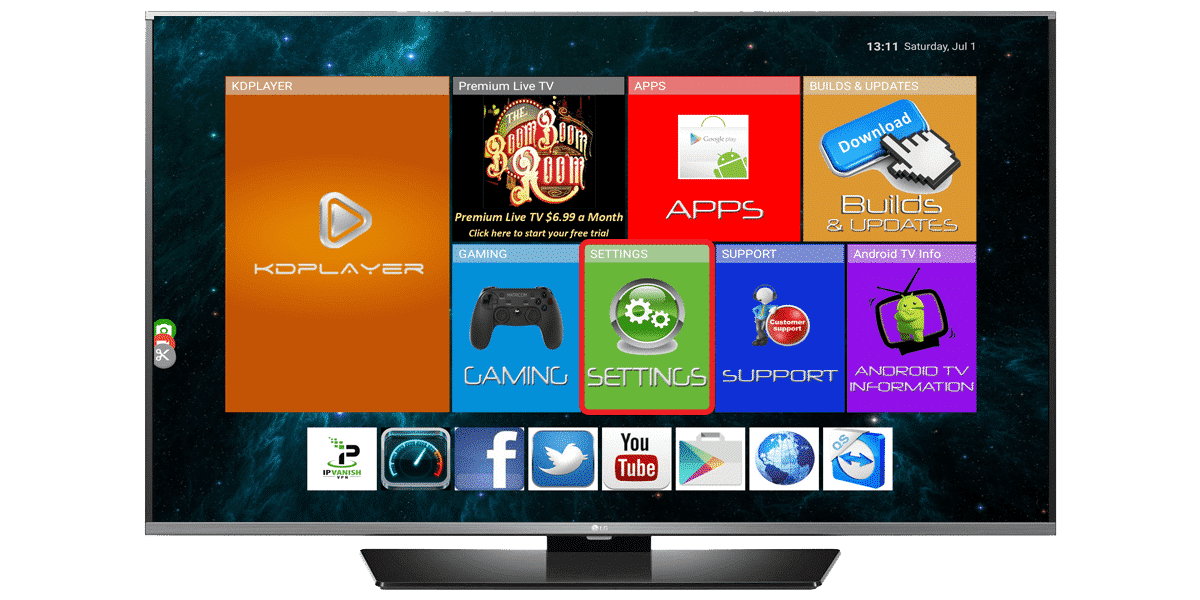
Upgrade your Android TV Box
In the beginning, most guys that were selling boxes would use an install wizard to install add ons directly on your box. The problem is that each box had to be serviced individually ever time an add-on closed it's doors which happens often.
Our new software KDPLAYER v4
Last year we developed our own software that allows us to push updates to all of our boxes across the internet. That in conjunction with your ability to reinstall your builds from our new interface solve 99% of our support issues. If your home screen does not look like the home screen to the left then you need to bring your box into one of our stores to be upgraded. If you are a current customer the upgrade is $25. If you have a box or a firestick that needs to be upgraded and you did not buy it from us the cost of the software update is $75.




















 Privacy
Privacy Security
Security Geo-Blocking
Geo-Blocking Legality
Legality



